Content of the article


Internet phishing is one of the most common modern online fraud schemes with a single goal: to obtain your confidential information. Attackers create fake websites, send out fake emails, links, and messages to trick you into entering your password, card information, or other personal details.
In this article, we will analyze what phishing is on the Internet, what types of phishing there are, how to quickly check a suspicious website for fraud, and what tools will help you protect yourself.
What is a phishing email?
It all starts with a single click. The user receives an email, SMS, or a message on a popular social network such as Instagram or Facebook. The letter contains a supposedly official request: «update your password», «confirm your transaction», «get a bonus». Inside the message is a link that looks like a regular URL of your bank’s website, delivery service, or social network. But in fact, it is a phishing link that implements the highest level of fraud.
The mechanism of the phishing link is as follows.
- Masking the website URL:
- by using similar characters. To commit fraud, individual letters in a domain name are substituted: «0» (zero) is substituted for «o», «l» (el) for «I» (i), «m» for «rn». For example, pr1vatbank.com or privatbank.com (where «a» is Cyrillic).
- through additional subdomains and hyphens. Sometimes extra words or hyphens are added, for example, login.privatbank-secure.com or privat-bank.com.login.verify. At first glance, it looks like an official subdomain, but in reality, the entire domain is fraudulent.
- using unusual extensions. Instead of the usual .com or .ua, they use .info, .xyz, .club, which do not raise suspicion among inattentive users, but indicate a fake.
- Redirection to a fake website:
- using an automatic redirect. When you click, you are instantly taken to a fake resource that looks like a real bank or delivery service website.
- cloning the website interface. Page templates, logos, fonts, and colors are all made as similar as possible. Even the browser address bar can show an SSL padlock if fraudsters have taken care of a free certificate.
- the presence of hidden scripts. On a phishing site, scripts are integrated into the page code that automatically intercept and encrypt the data entered by the user and send it to the attacker’s server instead of the bank’s official back-office system.
- Collection and transfer of your data:
- After the redirect, you will see a form where you are asked to enter your login, password, CVV, card expiration date, or code from an SMS message.
- As soon as you click «Login» or «Confirm», all form fields are encrypted and sent to the fraudulent server.
- Once they have your details, they can immediately withdraw money, sell the data on the black market, or use the account for new attacks.
This chain of online transactions – from the first email or click to the transfer of your data – is a typical type of phishing attack and guarantees fraudsters instant access to your sensitive information.
A phishing link is an elaborate fraudulent operation. The URL link is deliberately disguised as a familiar website, you click on it and enter confidential information, and the attackers immediately take it. So before you click on any link, take care of your security by checking the website address. It can save your data and money.
The key types of phishing schemes and basic principles of protection are described below.
Types of phishing and their differences
Today, fraudsters use different approaches on the Internet to force users to disclose their data. Let’s take a look at the main types of phishing and how they work.
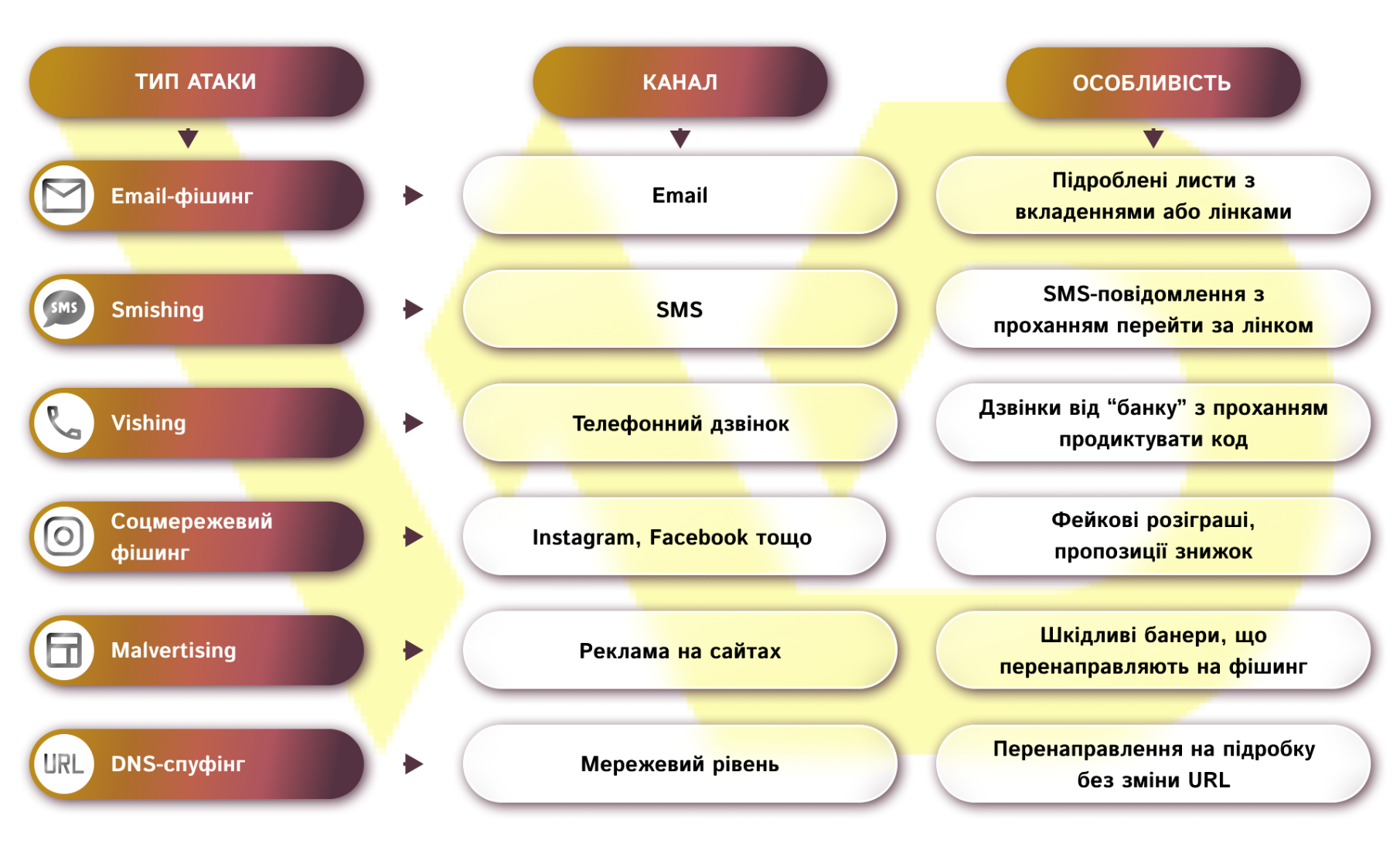
Email phishing
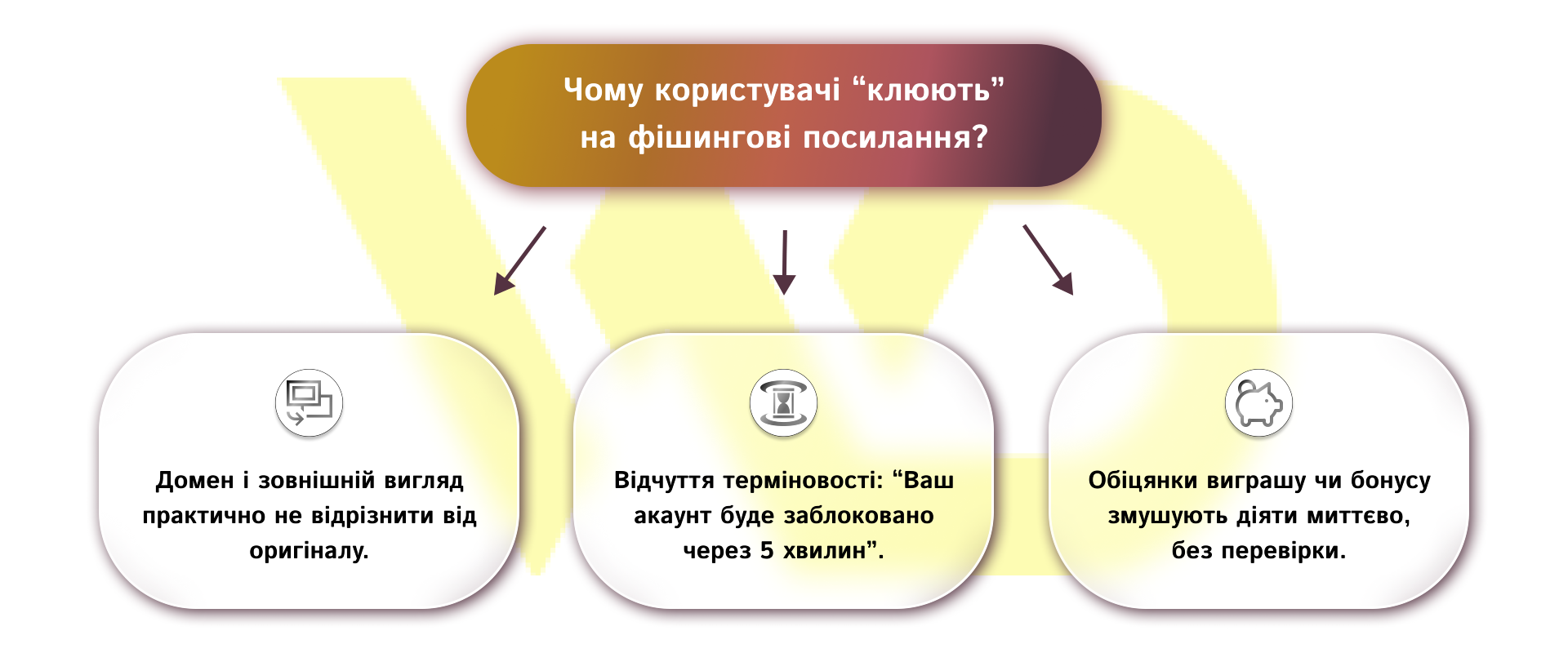
The most common online fraud scheme: an email is sent to your inbox, allegedly from a bank, postal service, or popular service. The subject line sounds urgent, for example: «Your account is blocked», «Security update required», «Get compensation». Inside the email, there is a link to a login form where you are asked to enter your username, password, and even CVV code. In fact, the user transfers this data to the fraudsters. This is a classic type of phishing attack that combines psychological pressure and technical disguise.
Smishing (SMS phishing)
I receive a message in the form of an SMS: «Your card is in danger of being blocked. Please follow this link to confirm». A click and the protection is broken; the user is taken to the mobile version of a fake bank website, where they enter their data. This is an example of how an online attack can start with a simple SMS.
Vishing (voice phishing)
Fraudsters call allegedly from the security service of a bank or government agency and ask for a code from an SMS or a card PIN to protect user data. As if «to verify the transaction». After that, the money may disappear without a trace.
Social network phishing
An attractive offer appears on Instagram, Facebook, or Telegram: a gadget giveaway, a free course, or an exclusive discount. To participate, you need to go to an external website and register. This is an example of how social media posts turn into a phishing attack, and users become victims of fraud.
Malvertising
Malicious fraudulent banners sometimes appear on popular news or entertainment sites. For example: «Check your PC security». After clicking, you can get to a resource disguised as an anti-virus utility, where you are encouraged to pay for a «license». This type of phishing uses ad networks to distribute malicious links.
DNS spoofing
The user enters the correct address of the bank in the Internet browser, but due to a changed DNS record on the Internet, he or she is directed to a fake website. The most unpleasant thing is that you may not even notice the spoofing until you enter your data. This is a technical example of a sophisticated phishing attack.
Each of these types of phishing uses a combination of psychological pressure (urgency, promises of winnings) and technical tricks (domain masking, interface clones). Knowing these signs will help you recognize the threat in time and avoid becoming a victim of fraud.
Statistics of phishing attacks on the Internet
According to the Anti-Phishing Working Group, 989,123 phishing attacks were recorded on the Internet in Q4 2024, which is 12% more than in the previous quarter. And 13% more than in the second quarter of 2024. In Q1, APWG counted 963,994 incidents, with the social media sector (Instagram, Facebook, etc.) remaining the most popular target (37.4% of attacks) and the SaaS/Webmail services segment the second most active (21%).
According to JumpCloud experts, fraudsters send about 3.4 billion phishing emails every day, each of which can become a «hook» for a user. At the same time, according to the CONTROL D article, 91% of cyberattacks begin with a phishing email, and more than 90% of malware reaches the victim through the mail. It’s also worth noting that according to a Hoxhant study, 74% of successful attacks are due to human error – a reckless click or data entry on a fake resource.
The reality of all the attack statistics is proved by an illustrative case covered by The Guardian. Back in 2013-2015, fraudsters withdrew more than $100 million from Facebook and Google accounts by forging emails on behalf of the Taiwanese supplier Quanta Computer. Both companies were able to recover most of the funds, but the incident proved that even tech giants are vulnerable to business phishing.
These figures prove that phishing on the Internet is not an isolated incident but a systemic threat. The following sections of the article will explain how to recognize a suspicious website in time and protect yourself from an attack.
Ways to identify a phishing site
Before entering any personal data on a website, you should make sure that it is really an official resource and not a cleverly disguised copy. Let’s look at how to check this yourself, what online tools to use, and why a dual approach saves you from phishing traps.
Manual scanning of phishing sites
- First, you need to look at the address in your browser. Genuine websites usually have a short domain, without unnecessary words, hyphens, or unusual endings such as .info or .xyz. If you see something like login.bank-secure.xyz or yourbank.com.club, it’s a reason to be wary.
- Then you need to click on the «lock» next to the URL. You can see who issued the SSL certificate and when it is valid. If the certificate is a well-known one (for example, Let’s Encrypt or DigiCert) and it contains the name of the company (EV SSL), this is a good sign. A complete lack of a certificate or a strange issuer is a very suspicious sign.
- View the page itself. The official service provides detailed contacts: physical address, business phone numbers, real email, and a detailed privacy policy with legal details. If the «Contacts» section is an empty form or contains nothing at all, there is definitely something wrong.
- It is important to have competent texts and calls to action. Phishing sites like to put emotional pressure: «Your account is blocked», «Urgently update your password!». Official companies rarely formulate messages with shouting and misspellings. This is another sign.
- It’s a good idea to check WHOIS: services like whois.com will show you the date of domain registration and the name (or hidden data) of its owner. If the site was created a few weeks ago and the owner is hidden behind a privacy service, this is a classic sign of bad faith.
- And finally, a bit of technical stuff: view the source code of the page (Ctrl+U). If you see scripts connecting from strange addresses, hidden iframes, or encrypted JavaScript that cannot be read, it’s best to stay away. This is a simple example of a deeper check.
Services for checking websites
To avoid relying on intuition alone, you can use proven online tools.
- VirusTotal allows you to paste any URL and instantly scan it against dozens of antivirus databases and blacklists.
- Google Safe Browsing will display a report on the domain’s reputation on the global network – whether it has been noticed in the distribution of malware or phishing.
- PhishTank works as a kind of «people’s registry»: volunteers add and verify suspicious sites, so one look at their database is often enough.
- URLVoid will complete the picture by analyzing the age of the domain, hosting, and mentions in various blacklists.
You should also install a browser extension (e.g. Netcraft Extension or Avira Browser Safety). They automatically block or warn you about known phishing resources before the page loads.
Important! No single method will provide a 100% guarantee of online protection, but a combination of manual verification and online services creates a reliable barrier. It is this multi-level approach that will allow you to protect your data, passwords, and finances even in the case of the most sophisticated phishing schemes.
For example, a combination of WHOIS checking, source code analysis, and VirusTotal scanning helped one company detect and block an attack on its website in time. This type of methodology is comprehensive; it is the only way to become an active participant in your own online protection, rather than a victim.
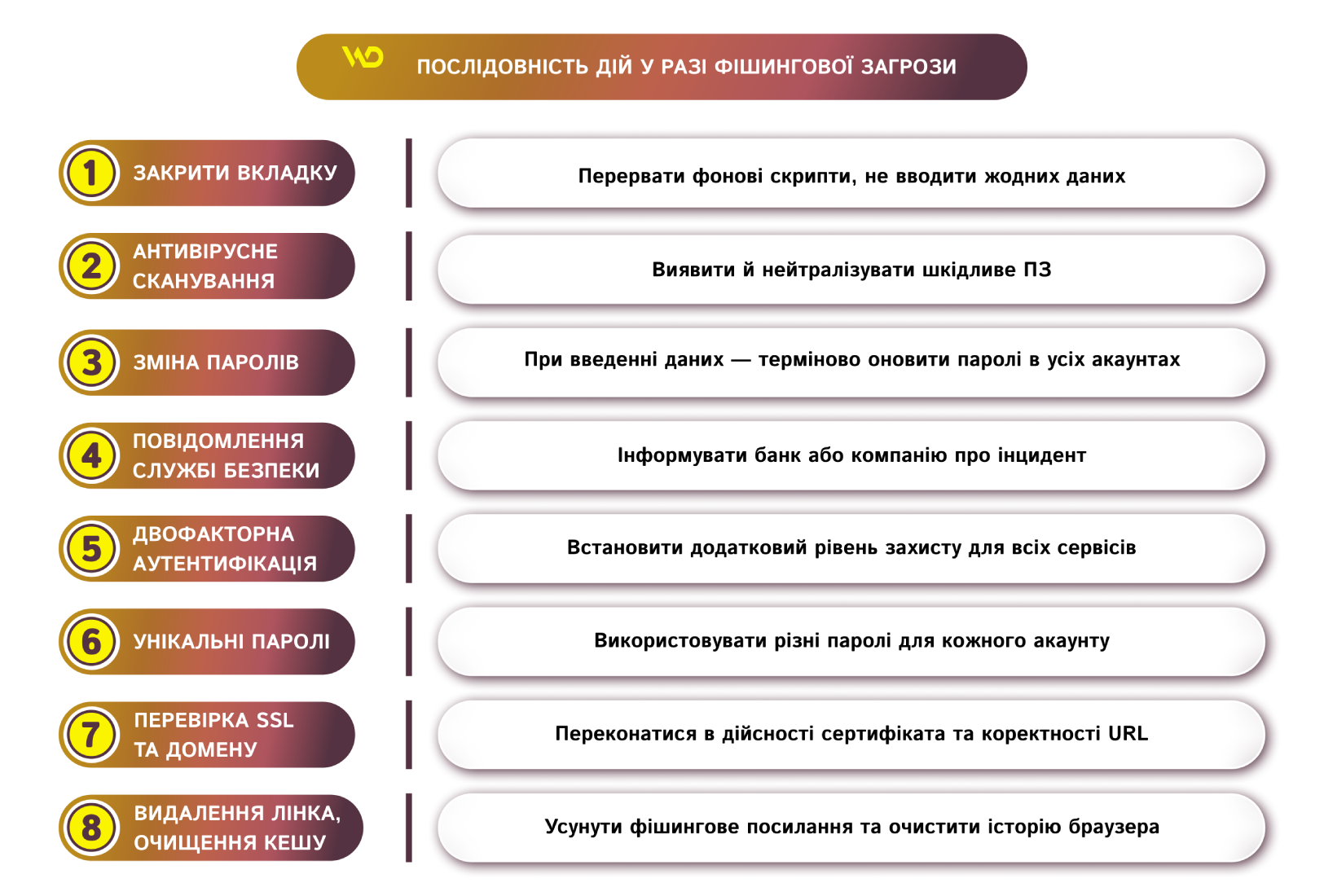
What should I do if I click on a phishing link?
If you accidentally click on a phishing link on the Internet, your first reaction should be to immediately close the browser tab or window to interrupt any background processes and scripts. It is important to refrain from entering any data – logins, passwords, or card details – even if the page continues to load. After that, you should run a full antivirus scan of your device to detect and neutralize possible malware from the Internet. If the data has been entered, you should immediately change the passwords on all affected accounts and notify the security service of the relevant bank or company of the incident.
How to protect yourself from phishing?
To protect yourself from phishing attacks in the future, you should:
- activate two-factor authentication on all services;
- use unique passwords;
- check the validity of the SSL certificate and the correctness of the domain before entering any confidential information.
An additional level of protection will be provided by a modern antivirus with an Internet protection module that will warn of suspicious pages in real time. It also requires regular updates on new phishing schemes and sharing this experience with colleagues and friends.
How to get rid of a phishing link?
If a phishing link does end up in your email or messenger, you should immediately delete it and clear your browser’s cache and browsing history. After such actions, the risk of further interaction with the malicious resource is minimized, and the combination of a timely response with preventive settings will ensure reliable data and financial protection.
For your convenience, here is a brief list of key steps to take in the event of a phishing threat to act quickly and consistently.
Conclusions
Internet phishing remains one of the most powerful and widespread threats in the modern online space, as it combines psychological manipulation and technical tricks. From a single phishing link to global malvertising campaigns, fraudsters are constantly coming up with new ways to deceive users and steal their confidential information. However, the knowledge gained about the mechanism of phishing schemes, the ability to recognize suspicious URLs and websites, as well as the regular use of multi-level verification (manual inspection of the domain, SSL certificate, WHOIS data, code analysis and online services) create a reliable «shield» against such attacks.
It is extremely important for active online users to take care of their protection and follow cybersecurity recommendations. This will make your online experience safer and allow you to stay one step ahead of fraudsters.







 06/08/2025
06/08/2025  1808
1808


