Content of the article
- /01 What is the admin panel and why is it needed?
- /02 Main types of admin panels
- /03 How to gain access legally and safely
- /04 Practical instructions and methods for restoring access
- /05 Setting up security for the admin area
- /06 Organizing team accesses
- The principle of Least Privilege
- Procedure for requesting and registering access
- Temporary rights and mechanisms for their automatic removal
- Onboarding and offboarding
- Logging, auditing, and periodic revision of rights
- Emergency access procedure
- Tools and practices that simplify access management
- Training and policies

Understanding the structure of the admin panel and access rules is critical for business owners, marketers, and developers today, as it allows them to respond quickly to security incidents, effectively coordinate remote teams, and ensure the continuity of business processes.
In this article, we will consider what an admin panel is and what types of them exist, standard login paths and legal ways to restore access, practical steps in case of access loss, basic and advanced security measures.
What is the admin panel and why is it needed?
The admin panel is the «control center» of the site. It combines:
- content management tools: editing pages, publishing posts;
- technical tools: updating plugins, themes, cache settings;
- business functions: order management in the online store;
- access control mechanisms: roles and rights.
Through the admin panel, technical specialists and managers control the site’s workflows, and owners receive up-to-date information about the project status. The interfaces differ for different roles: a developer needs tools to access files and a database, a marketer needs access to SEO plugins and statistics.
Main types of admin panels
Let’s look at the types of admin panels and what are their fundamental differences. It depends on what tools and rights you need to work, what security risks you should consider, and what steps to restore access will be relevant in a particular situation.
CMS (content management systems)
The most popular are WordPress, OpenCart, PrestaShop, and Magento. Such admin panels are focused on working with content:
- creating and editing pages;
- menu management;
- publishing posts;
- customization of plugins and themes.
Usually, the login is organized through a web form on a specific URL (in WordPress, it is usually /wp-admin or /wp-login.php), but many projects change the standard paths or add additional layers of protection. CMS admin panels are most often used by content managers, marketers, and editors; for developers, the ability to work through plugins, APIs, or console tools is more important.
WordPress is a convenient CMS, but without SEO, its potential remains untapped.
The WEDEX team knows how to promote WordPress sites so that they consistently grow in Google search results. We will help you improve your visibility in search results — from technical SEO to content optimization and loading speed.о
Hosting and server panels
For example, cPanel, Plesk, or WHM. These interfaces work at the infrastructure level:
- access to the file system;
- database management;
- setting up mail;
- creating and restoring backups;
- domain and SSL management.
Unlike CMS, the hosting panel is not responsible for the content of the site, but provides tools for maintaining the environment. System administrators and hosting engineers usually have access to such panels. In case of loss of access, it is through the hoster panel that recovery is often the fastest.
Custom back offices
For complex products, such as proprietary CRM, SaaS solutions, or corporate portals, individual admin panels with unique roles, authorization logic, and internal URLs are created. Such solutions are tailored to the needs of the business and can include both content management tools and advanced analytics and integration modules. Access to custom back offices is usually customized individually.
Now that the classification and key differences are clear, let’s move on to practical scenarios – how to get access to the admin panel in each of these cases.
How to gain access legally and safely
Before looking for ways to access the admin panel, it is important to define your role and legal status.
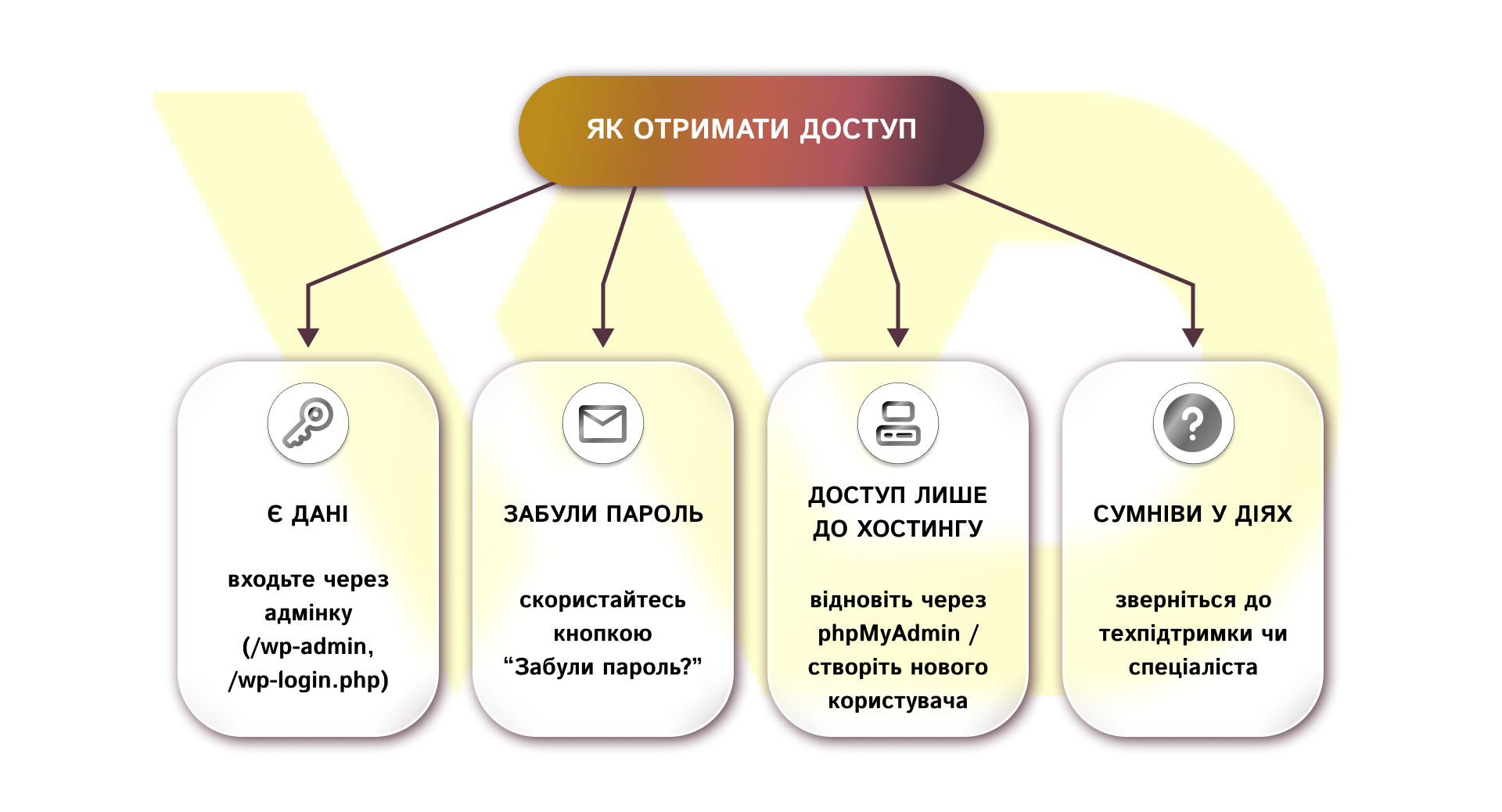
And now let’s go into more detail.
Incorrect steps create risks for the stability of the site and may violate the host’s terms of service or legislation. Therefore, first choose a legal and safe way – from simple login to recovery mechanisms through the hosting, depending on your situation. Let’s consider the options:
- You have the credentials.
Open the login form through a standard or custom URL and enter your username and password. Next, go through two-factor authentication if it is configured. This is the fastest and least risky scenario. For WordPress, the typical path is /wp-admin or /wp-login.php. If you are working in a team, make sure you use corporate credentials or a dedicated account with the necessary rights.
- Forgot your password.
If you remember your login or registered email, click «Forgot your password?» on the login page and enter your email or login. The system will immediately send you a link to reset your password. This is the recommended and safest way in most CMSs, as it saves the change log and minimizes the risk of errors when manually editing. Make sure that the mailbox to which the email is sent belongs to an authorized person or company.
- You are the owner of the domain/hosting, but you do not have any credentials in the CMS.
If you have confirmed ownership of the hosting or domain, the most reliable way is to restore access through the hosting panel. Through the hoster’s tools, you can access phpMyAdmin, create a new administrator in the database, or change the password in the user profile. Before any operations, be sure to make a full backup of your website and database and, if possible, work in close coordination with your host’s technical support or development team.
Anyone who is unsure of their actions is advised to contact technical specialists, as incorrect changes to the database or website files may result in data loss or resource downtime.
Practical instructions and methods for restoring access
You should move on to more «technical» methods of restoring access only if the invasive ones have failed. Manual edits to the database or interference with site files is a last resort. Below are step-by-step scenarios for the most common cases.
WordPress
The first and easiest step: on the login page (/wp-login.php or /wp-admin), click «Forgot your password?». This option has already been analyzed above.
If you have access to the server via SSH and have WP-CLI installed, you can quickly change the password or create a new administrator with the command, for example wp user update admin –user_pass=«NewStrongPassword123»!. This method is convenient for developers and hosting engineers – it does not require manual database editing and reduces the risk of errors.
If other methods do not work and you do not receive emails, you can use phpMyAdmin to: backup the database: go to the wp_users table, find the administrator record, and update the user_pass field. It is important to keep in mind that WordPress uses modern password hashes, so a direct replacement with MD5 is not recommended for current versions. It is safer to create a new administrator via SQL or use the WP-CLI. Before editing the database on the production site, be sure to make a full backup and, if possible, test the procedure on a local copy.
Other CMS (OpenCart, PrestaShop, Magento)
The general logic of recovery is the same: try a standard reset via email. If it doesn’t help, then restore through the hoster’s tools or through the database. In complicated cases, please contact the technical support of the platform or developer.
It is also worth noting that specific SQL queries and processes depend on the CMS and its version; therefore, it is advisable to use the official documentation of the platform or instructions from trusted resources for the corresponding system.
Access through the hosting panel
If you have access to your hosting account, this is often the fastest and most reliable way to restore access:
- make a full backup (files + database);
- open phpMyAdmin through the panel and create or update an administrator or restore the database from the backup;
- check and, if necessary, change FTP/SFTP credentials;
- if files are damaged, restore them from a backup;
- review error logs to diagnose the causes of access loss.
Restoring access is a process in which it is important to follow a sequence: from the least risky methods to the more technical ones. The key rules are to make backups before any manipulations, document the actions taken, and, if possible, coordinate with the host’s technical support or developer.
After access is restored, the priority should be to strengthen the security of the admin panel, which we will consider next.
Setting up security for the admin area
The admin area is a high-risk zone. Protection should be multi-level:
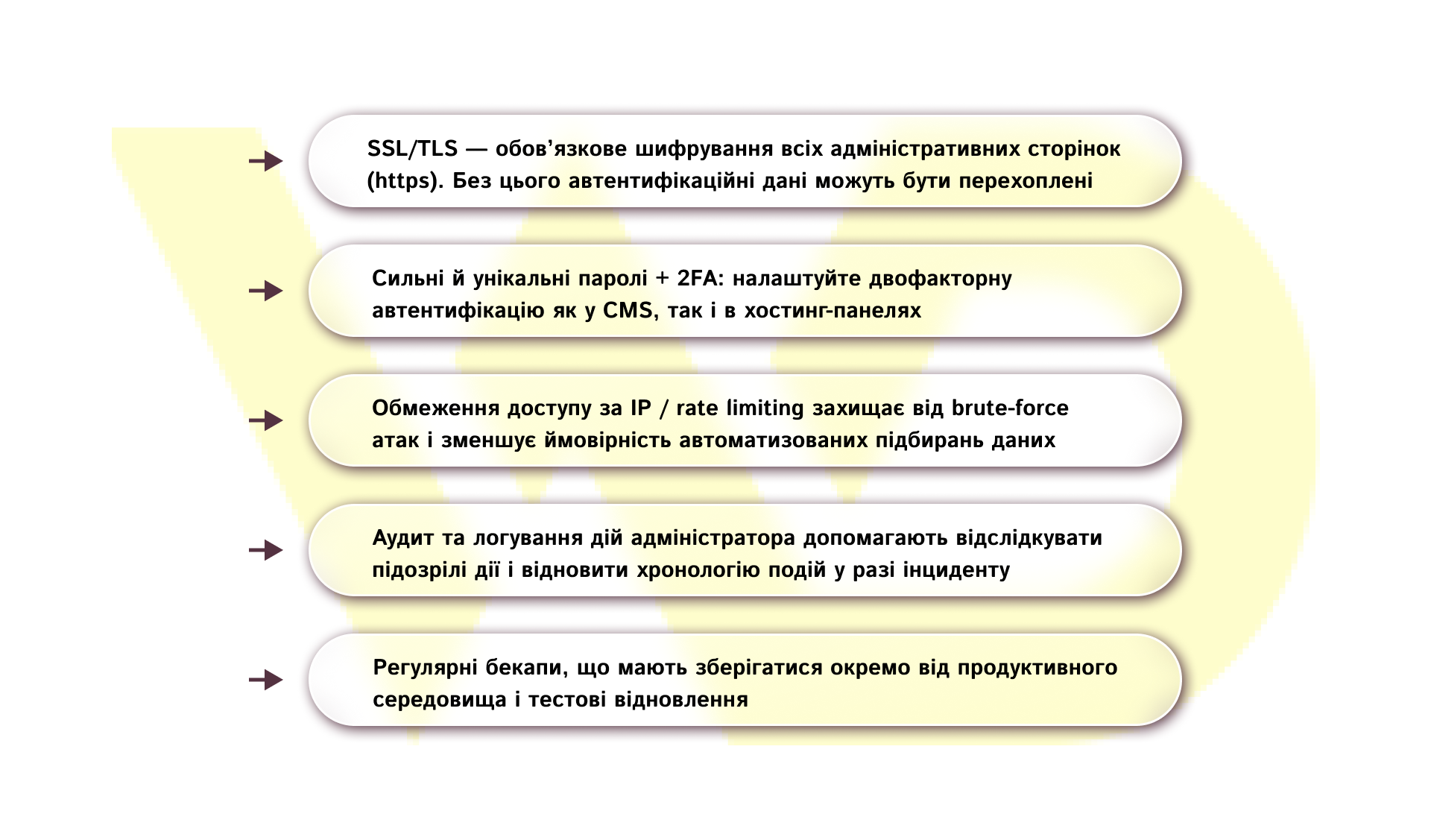
A comprehensive approach to admin security is not a set of one-time settings, but an ongoing process. Remember that even one missed option can negate other security measures.
And despite all the steps taken to secure the admin panel, it’s still not a guarantee of security if the team’s access is not organized properly. So let’s look at this issue in the next section.
Organizing team accesses
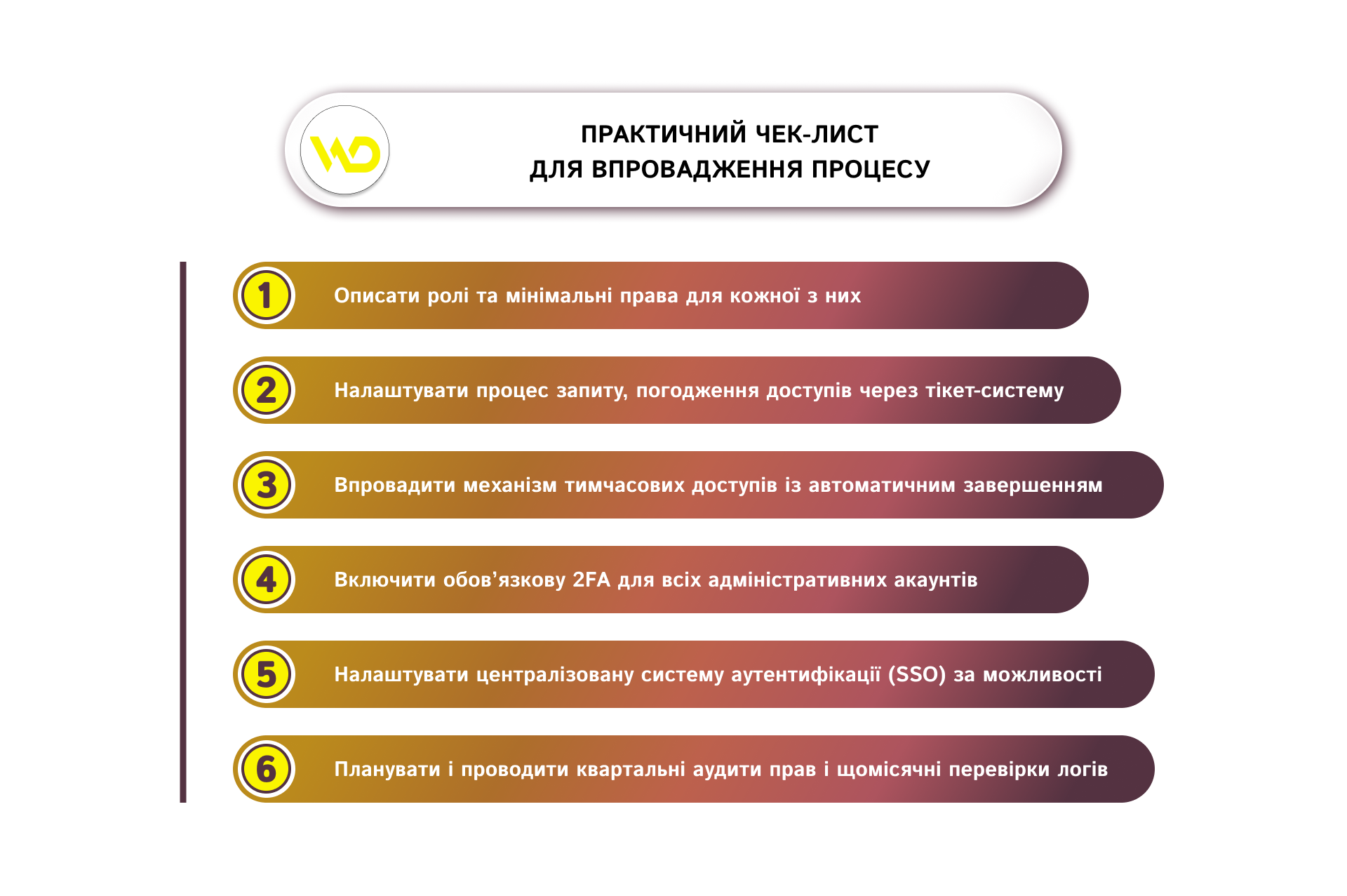
To minimize the human factor and the risk of abuse, implement a formalized access management process that combines technical settings and organizational procedures.
The principle of Least Privilege
Grant only those rights that are necessary to perform specific tasks. For example, a marketer should be granted access to the content editor and SEO tools, but not the ability to install or remove plugins. A content manager needs permissions to create and edit pages and posts, as well as manage media files. The developer should be granted access to FTP/SFTP, SSH, and the database, but only temporarily and for specific tasks. An analyst should have access to analytics and statistics tools, but not the ability to change the platform’s administrative settings.
To simplify security management, access should be realized through roles and groups rather than by individually setting up rights.
Procedure for requesting and registering access
Implement a formal workflow (an internal ticket or application) with the following required fields
- purpose of access
- description of the work,
- expected dates (from and to),
- access level (role),
- approval from a responsible person (owner or manager).
Require confirmation of task completion and access closure upon completion of work.
Temporary rights and mechanisms for their automatic removal
To perform unscheduled work, you should create temporary accounts or use tokens or sessions with a limited validity period. And after a certain period or confirmation of the task completion, access rights should be automatically removed. To do this, it is advisable to use tools that support one-time access or timed delegation, such as SSO services or identity management systems that provide a just-in-time access mechanism.
Onboarding and offboarding
During onboarding, you should perform identity verification, grant the new user only the rights that are really needed to perform their duties, provide security policy briefings, and make sure to enable two-factor authentication (2FA). During the offboarding process, you should immediately remove all access upon termination or end of contract, change common passwords, revoke tokens, and review related integrations to prevent unauthorized use of resources.
Logging, auditing, and periodic revision of rights
Keep a log of administrator activity, recording who performed what actions, when, and how. Check the list of active accounts and their permissions regularly, for example, quarterly, deleting or restricting those that are not being used. Also, conduct periodic security audits and test restores of backups to ensure you are prepared for incidents.
Emergency access procedure
Define a clear mechanism for emergency access, i.e. who can initiate, who has to approve after the fact, how to document the actions. Such sessions should be temporary, as transparent as possible and fully documented.
Tools and practices that simplify access management
Use centralized identity management solutions (SSO, LDAP, OIDC) as this reduces the number of accounts and simplifies access disabling. Additionally, implement password managers and secret managers to avoid manually storing passwords in email or text files. And enforce key/password rotation for service accounts and integrations.
Training and policies
Create clear policies on access, secrecy, and incident response. Also, conduct regular trainings for employees on how to work safely with the admin panel.
An organized and controlled access system is the last, but critical layer in the website security chain. The combination of technical measures with streamlined processes allows you to reduce the risk of abuse and respond quickly to incidents without losing the resource’s performance.
Remember: knowing how to get access is important, but managing it confidently and safely is even more important.






 06/10/2025
06/10/2025  1668
1668



